Penetration Testing & Incident Response
Master penetration testing and incident response to proactively safeguard your organization’s network.
Penetration testing and incident response are critical components of a comprehensive cybersecurity strategy. This course will teach you how to simulate real-world attacks to identify vulnerabilities and prepare you to respond effectively when a security incident occurs. Through hands-on exercises and expert-led training, you’ll gain the skills needed to uncover weaknesses and swiftly mitigate threats to protect your organization’s data and systems.
What is Penetration Testing ?
Penetration Testing, often referred to as pen testing, is a proactive cybersecurity practice used to identify and evaluate vulnerabilities in an organization’s systems, networks, or applications. It involves simulating real-world cyberattacks to uncover weaknesses that attackers could exploit, allowing organizations to address these issues before they are compromised.
Penetration testing is typically performed by ethical hackers or security professionals who use the same tools and techniques as malicious hackers but with authorization from the organization. The goal is to enhance the security posture by identifying flaws, such as unpatched software, misconfigurations, or weak passwords, and providing recommendations for mitigating these risks.
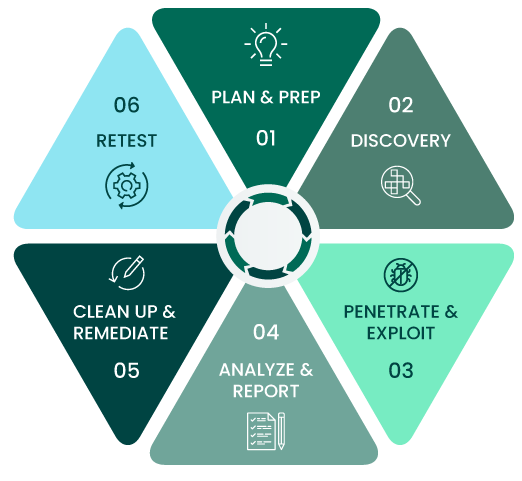
Key Steps in Penetration Testing
- Planning and Reconnaissance: The tester gathers information about the target system, including its architecture, network topology, and potential entry points.
- Scanning and Vulnerability Analysis: Tools are used to scan the system for vulnerabilities, identifying weak spots in the network or software.
- Exploitation: The tester attempts to exploit identified vulnerabilities to assess the potential damage a real attack could cause.
- Reporting: A detailed report is provided, outlining the vulnerabilities discovered, their severity, and steps for remediation.
Why Penetration Testing is Important
- Identifies Vulnerabilities: Helps organizations discover and address security gaps before they are exploited by malicious actors.
- Enhances Security: Strengthens overall security posture by fixing weaknesses and improving defenses.
- Meets Compliance Requirements: Many regulations and standards, such as PCI DSS or ISO 27001, mandate regular penetration testing.
- Prepares for Real Attacks: Simulates real-world attack scenarios, helping organizations understand their readiness and response capabilities.
What the Course Offers ?
Understanding Penetration Testing Methodology
“Learn the steps of a penetration test, from reconnaissance to exploitation and reporting, and understand how to ethically simulate attacks to identify vulnerabilities.”Tools and Techniques for Penetration Testing
“Get hands-on experience with industry-standard tools like Kali Linux, Metasploit, Burp Suite, and others to conduct penetration tests and exploit weaknesses.”Vulnerability Assessment
“Learn how to perform thorough vulnerability assessments to identify weaknesses in systems, networks, and applications that could be exploited by attackers.”Incident Response Planning and Management
“Understand how to prepare an incident response plan (IRP), identify the stages of an incident, and respond to security breaches effectively to minimize damage.”Forensic Analysis and Evidence Gathering
“Gain skills in forensic analysis to investigate security incidents, collect evidence, and document findings for legal and compliance purposes.”Malware Analysis and Reverse Engineering
“Learn techniques for analyzing malware and reverse engineering its code to understand how it works, how it spreads, and how to mitigate its effects.”Post-Incident Recovery and Reporting
“Master the process of recovery after an incident, including system restoration, reporting to stakeholders, and improving security measures to prevent future attacks.”
Our Approach
Our course delivers three key components
Comprehensive Penetration Testing Process
- What You’ll Learn:
“Master the full penetration testing lifecycle, including planning, information gathering, vulnerability analysis, exploitation, and reporting.” - Why It’s Important:
“Understanding the penetration testing process helps you simulate realistic attacks to identify security flaws and prioritize remediation efforts.”
Incident Response Framework and Preparation
- What You’ll Learn:
“Learn how to develop an incident response plan, identify security breaches, contain threats, and recover from attacks with minimal disruption.” - Why It’s Important:
“Having an effective incident response framework in place ensures that your organization can react swiftly and decisively when faced with a cyberattack.”
Post-Incident Analysis and Continuous Improvement
- What You’ll Learn:
“After responding to an incident, you’ll learn how to conduct post-incident analysis, gather evidence, and make necessary improvements to your organization’s security measures.” - Why It’s Important:
“Post-incident analysis helps you identify what went wrong, improve response strategies, and strengthen defenses to prevent future breaches.”
Benefits of This Course
Hands-On Penetration Testing Skills
Gain practical experience using penetration testing tools and techniques to identify vulnerabilities and conduct ethical hacking exercises.
Real-World Incident Response Techniques
Learn how to respond to and manage security incidents in real-time, reducing the risk and impact of cyberattacks on your organization.
Industry-Standard Tools and Best Practices
Get familiar with industry-standard tools like Metasploit, Nmap, and Wireshark, and learn best practices followed by top cybersecurity professionals.
Prepare for Cybersecurity Certifications
Prepare for certifications such as Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), and GIAC Certified Incident Handler (GCIH).
Improve Security Posture and Risk Management
By mastering both penetration testing and incident response, you’ll be able to proactively identify and mitigate security risks before they turn into threats.
Enhanced Career Opportunities
Enhanced Career Opportunities
Real-World Simulations
Participate in hands-on labs and real-world simulations to practice penetration testing and incident response, allowing you to develop practical, job-ready skills.
Conclusion
Penetration testing and incident response are essential for any organization aiming to protect its data, systems, and networks from cyber threats. This course offers a hands-on approach to learning the key skills needed to assess network security, identify vulnerabilities, and effectively respond to security incidents. Whether you’re preparing for a certification or aiming to improve your organization’s security posture, this course provides the tools and knowledge to succeed in the fast-evolving cybersecurity field. Start your training today and take the first step toward becoming a cybersecurity expert!